Information Security
ISO 27001:2022
Section Links:
ISO 27001 - Information Security.
Reviewed: 27th September 2024.
ISO/IEC 27001 is an international standard that provides a framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). It is published jointly by the International Organisation for Standardisation (ISO) and the International Electrotechnical Commission (IEC).
Here’s an overview of its key aspects:
Information Security Management System (ISMS):
ISO/IEC 27001 outlines the requirements for a systematic approach to managing sensitive company information, ensuring its confidentiality, integrity, and availability. This includes managing risks related to people, processes, and IT systems by applying appropriate security controls.Risk Management Framework:
A core component of ISO/IEC 27001 is risk management. It helps organisations assess information security risks and implement appropriate controls to mitigate these risks based on their impact and likelihood.Annex A – Security Controls:
ISO/IEC 27001 includes a set of security controls listed in Annex A, which serve as best practices for managing information security. These controls cover various domains like access control, cryptography, physical security, and incident management.Certification:
Organisations can get certified against ISO/IEC 27001 by undergoing an independent audit by accredited certification bodies. Certification demonstrates that the organisation has implemented robust information security management practices in line with international standards.Continual Improvement (PDCA Cycle):
ISO/IEC 27001 follows the Plan-Do-Check-Act (PDCA) cycle to ensure continuous improvement. This means organisations regularly review and update their security controls to adapt to evolving risks.Applicability Across Sectors:
The standard is applicable to organisations of all sizes and sectors. It helps in demonstrating compliance with regulations and building trust with customers by showing a commitment to protecting sensitive information.
By adopting ISO/IEC 27001, organisations can effectively protect their data and meet legal, regulatory, and contractual obligations related to information security.
The benefits of ISO 27001
ISO/IEC 27001 certification provides organisations with a structured framework to manage sensitive information securely. This internationally recognised standard helps in establishing, implementing, maintaining, and improving an information security management system (ISMS). The certification offers several key benefits:
1. Enhanced Security Posture
- Systematic Risk Management: ISO/IEC 27001 requires organisations to identify risks, threats, and vulnerabilities and implement appropriate security controls to mitigate them.
- Structured Approach: It provides a framework to manage information security risks systematically, ensuring data protection, minimising breaches, and reducing potential security incidents.
2. Regulatory Compliance
- Global Recognition: Compliance with ISO/IEC 27001 helps organisations meet various legal, regulatory, and contractual requirements, such as GDPR, HIPAA, or other data protection laws.
- Reduced Fines: Organisations certified to ISO 27001 are more likely to meet these regulations, reducing the risk of penalties from regulatory bodies.
3. Improved Customer and Stakeholder Trust
- Credibility and Confidence: ISO/IEC 27001 certification demonstrates that an organisation is committed to securing customer data, boosting trust and credibility.
- Competitive Advantage: The certification can set a company apart from its competitors, showcasing its dedication to safeguarding sensitive information.
4. Business Continuity
- Proactive Risk Management: By identifying potential risks to information assets, the standard helps prepare for and respond effectively to incidents, ensuring continuity of critical business functions.
- Disaster Recovery: ISO 27001 also emphasises creating disaster recovery and incident response plans, enabling faster recovery from potential disruptions.
5. Operational Efficiency
- Clear Policies and Procedures: Implementing ISO/IEC 27001 promotes the development of clear policies and procedures related to information security, leading to improved efficiency.
- Reduced Costs: By minimising security incidents and breaches, organisations can avoid costs associated with data loss, downtime, and legal liabilities.
6. Employee Awareness and Accountability
- Security Culture: ISO 27001 ensures that employees across the organisation are trained in security best practices, fostering a culture of security awareness.
- Defined Roles and Responsibilities: It clearly defines roles and responsibilities for information security, increasing accountability and reducing human errors.
7. Third-Party Assurance
- Supply Chain Confidence: Organisations with ISO/IEC 27001 certification can demonstrate their security compliance to third parties, making it easier to do business with clients, partners, or suppliers.
- Vendor Trust: Vendors and partners are more likely to trust a certified organisation with their data, improving business relationships.
8. Continuous Improvement
- Ongoing Risk Assessment: ISO/IEC 27001 promotes regular reviews and updates of the ISMS, ensuring the system evolves with emerging threats and business needs.
- Audit Readiness: Regular audits are part of the certification, which drives continuous improvement of the organisation’s security processes.
9. Global Competitiveness
- International Benchmark: ISO/IEC 27001 is recognised worldwide, making it easier for organisations to expand and operate internationally with consistent information security practices.
- Access to New Markets: Many global contracts and tenders require ISO 27001 certification, giving businesses access to new markets that prioritise data security.
10. Reduced Insurance Premiums
- Lower Cybersecurity Insurance Costs: By demonstrating strong cybersecurity practices, organisations may benefit from lower insurance premiums as the risk of data breaches is reduced.
Summary
ISO/IEC 27001 certification enhances an organisation’s security posture, builds customer trust, ensures regulatory compliance, and contributes to business continuity and operational efficiency. This makes it a strategic tool for businesses of all sizes in today’s digital landscape.
Mandatory Documents.
ISO/IEC 27001 is a global standard for establishing, implementing, maintaining, and continuously improving an information security management system (ISMS). To comply with ISO 27001, certain mandatory documents are required, while others may be created as part of the organisation’s ISMS documentation. The mandatory documents are critical to demonstrate compliance during an audit.
Here are the mandatory documents required by ISO/IEC 27001 (2013 and 2022 editions):
1. Scope of the ISMS (Clause 4.3)
- Defines the boundaries and applicability of the ISMS to the organisation.
- This document outlines what is covered and what isn’t under the ISMS.
2. Information Security Policy (Clause 5.2)
- States the high-level intentions and objectives regarding information security within the organisation.
- It includes the commitment to continuous improvement and compliance with relevant security requirements.
3. Risk Assessment Process (Clause 6.1.2)
- Describes the methodology for identifying risks, including how risks are assessed, prioritised, and treated.
- A formal, documented risk assessment process helps in understanding the risks to information security.
4. Risk Treatment Plan (Clause 6.1.3)
- A plan that specifies how identified risks will be treated (mitigated, transferred, accepted, or avoided).
- This plan includes the decisions on risk treatment options and the application of security controls.
5. Statement of Applicability (Clause 6.1.3, A.6-A.18)
- Lists the ISO 27001 Annex A controls, identifies which controls are applicable to your ISMS, and justifies why any control is excluded.
- It serves as a key document in an audit, demonstrating the organisation’s decision-making regarding controls.
6. Risk Assessment Report
- A detailed report summarising the findings of the risk assessment.
- This document may not be explicitly mentioned in the standard, but auditors typically expect to see it.
7. Risk Treatment Report
- A record of how each risk has been treated, matching the risk treatment plan.
- It details actions taken to implement controls and mitigate risks.
8. Definition of Security Roles and Responsibilities (Clause 5.3)
- Documents outlining responsibilities and roles related to information security.
- Clear definitions of accountability ensure that everyone understands their security responsibilities.
9. Inventory of Assets (A.8.1.1)
- A list of all information assets (e.g., data, systems, hardware) within the scope of the ISMS.
- This helps in identifying what needs protection and where risks may exist.
10. Access Control Policy (A.9.1.1)
- A policy that defines how access to information and information systems is managed and controlled.
- The policy ensures that only authorised personnel have access to sensitive information.
11. Acceptable Use Policy (A.8.1.3)
- Specifies acceptable and unacceptable use of information systems by employees.
- Ensures that employees are aware of security requirements and practices.
12. Monitoring and Measurement Plan (Clause 9.1)
- Documents how the performance of the ISMS will be monitored and measured.
- It includes what metrics are used and how results will be reported.
13. Internal Audit Program and Results (Clause 9.2)
- A documented plan and record of ISMS audits, including schedules, procedures, and results.
- Internal audits verify compliance with ISO 27001 and identify areas for improvement.
14. Non-conformities and Corrective Action (Clause 10.1)
- A record of any non-conformities identified (e.g., during internal audits) and how they were addressed.
- It includes the root cause analysis and steps taken to prevent reoccurrence.
15. Training and Awareness Records (Clause 7.2)
- Documentation that demonstrates that employees have been trained in information security and are aware of security policies and procedures.
16. Records of Results of Risk Treatment (Clause 6.1.3)
- A document that records how each security risk has been addressed, including what treatments were selected and implemented.
17. Evidence of Competence (Clause 7.2)
- Records proving that personnel responsible for information security have the necessary competencies (skills, qualifications, and experience).
18. Document Control (Clause 7.5)
- Describes how ISMS documents are controlled, including how they are created, reviewed, updated, and distributed.
- Ensures proper document management across the organisation.
19. Records of Communication (Clause 7.4)
- Records of internal and external communications related to the ISMS.
- Ensures that relevant information is communicated effectively across the organisation.
20. Results of the Management Review (Clause 9.3)
- A documented record of management reviews conducted periodically to ensure the ISMS remains effective and aligned with business objectives.
21. Evidence of Continual Improvement (Clause 10.2)
- Documents showing how the organisation continuously improves its ISMS.
- This includes any changes made as a result of audits, reviews, or incident investigations.
Note: These documents are mandatory for compliance, but organisations can also create additional documentation depending on their specific needs and the complexity of their ISMS.
Mandatory Records.
The ISO/IEC 27001:2022 standard outlines the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). Part of these requirements involves maintaining specific mandatory documented information (records), which provide evidence of the operation and effectiveness of the ISMS.
Here is a list of mandatory records required by ISO/IEC 27001:2022:
1. Scope of the ISMS
- A documented description of the scope of the ISMS, outlining what is covered and what is excluded.
2. Information Security Policy
- A documented information security policy, including the objectives for information security.
3. Risk Assessment and Treatment Process
- Records showing how risks are identified, evaluated, and treated. This includes the risk methodology and criteria for accepting risks.
4. Statement of Applicability (SoA)
- A record listing all the controls selected from Annex A of ISO/IEC 27001 and justifying the selection or exclusion of each control.
5. Risk Treatment Plan
- Documented information outlining how the identified risks will be treated, the responsible individuals, and the timeline for treatment.
6. Risk Assessment Report
- Results and reports from risk assessments carried out on the organisation.
7. Evidence of Competence
- Records demonstrating that personnel have the necessary competence for their ISMS roles, including training records, certifications, or experience.
8. Monitoring and Measurement Results
- Documented results of the monitoring and measurement of the ISMS, which might include internal audits, reviews of security incidents, and operational metrics.
9. Internal Audit Program and Results
- An internal audit plan and results from internal ISMS audits, which confirm whether the system conforms to requirements.
10. Nonconformities and Corrective Actions
- Records of any nonconformities identified during the operation of the ISMS and actions taken to correct them.
11. Management Review Results
- Documented evidence of management reviews, including discussions of ISMS performance, results of audits, and decisions on continual improvement.
12. Evidence of Information Security Incidents
- Records of information security incidents, including the investigation and results of corrective actions taken.
13. Access Control Records
- Documented evidence showing the implementation of controls related to user access, such as who has access to what and how access is managed.
14. Evidence of Operational Planning and Control
- Records of activities and processes to ensure the ISMS continues to meet security objectives, including documentation related to asset management, communication protocols, and supply chain management.
15. Supplier Monitoring and Evaluation
- Records showing how external suppliers and partners are evaluated and monitored concerning information security.
16. Cryptographic Key Management
- Records of how cryptographic keys are managed, including who has access to the keys and how they are used or stored.
Each organisation may have more records depending on its specific context, risks, and legal or contractual obligations, but these records are explicitly required to maintain compliance with ISO/IEC 27001:2022. Maintaining these records is critical for internal management as well as for certification audits.
Clauses.
The ISO/IEC 27001:2022 standard is an updated version of ISO/IEC 27001, the international standard for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). The 2022 revision introduces some refinements and modifications compared to the earlier version (ISO/IEC 27001:2013). Below is an outline of the key clauses in the ISO/IEC 27001:2022 standard.
ISO/IEC 27001:2022 Clauses
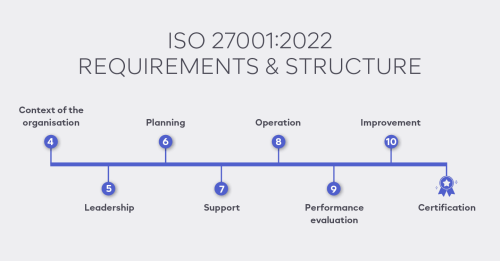
ISO/IEC 27001:2022 consists of 10 main clauses and an Annex A that contains a set of security controls.
Clause 0 – Introduction
This clause introduces the standard and its purpose. It outlines the importance of information security, including how the standard helps to manage and mitigate security risks.
Clause 1 – Scope
This defines the applicability of the standard. It specifies the standard’s scope, which covers requirements for establishing, implementing, maintaining, and continually improving an ISMS within the context of the organization.
Clause 2 – Normative References
This clause refers to other documents that are indispensable for the application of ISO/IEC 27001. For this standard, it generally refers to ISO/IEC 27000, which provides an overview and vocabulary for the ISMS family of standards.
Clause 3 – Terms and Definitions
This clause explains key terms and definitions used throughout the standard. It typically relies on definitions found in ISO/IEC 27000.
Clause 4 – Context of the Organization
This clause requires an organization to understand its context and the interested parties relevant to its ISMS. Key sub-clauses include:
- 4.1 Understanding the organization and its context
- 4.2 Understanding the needs and expectations of interested parties
- 4.3 Determining the scope of the ISMS
- 4.4 ISMS and its processes
Clause 5 – Leadership
This clause defines the role of leadership in establishing and supporting the ISMS. It emphasizes the need for top management to demonstrate commitment. Key sub-clauses include:
- 5.1 Leadership and commitment
- 5.2 Information security policy
- 5.3 Organizational roles, responsibilities, and authorities
Clause 6 – Planning
This clause focuses on the planning necessary to establish and implement the ISMS. It includes risk management and setting information security objectives. Key sub-clauses include:
- 6.1 Actions to address risks and opportunities
- 6.1.1 General
- 6.1.2 Information security risk assessment
- 6.1.3 Information security risk treatment
- 6.2 Information security objectives and planning to achieve them
- 6.3 Planning of changes
Clause 7 – Support
This clause outlines the resources, competence, awareness, communication, and documentation required to support the ISMS. Key sub-clauses include:
- 7.1 Resources
- 7.2 Competence
- 7.3 Awareness
- 7.4 Communication
- 7.5 Documented information
Clause 8 – Operation
This clause focuses on the implementation and operation of the ISMS. It covers the management of information security risks and ensures that processes are in place to meet information security objectives. Key sub-clauses include:
- 8.1 Operational planning and control
- 8.2 Information security risk assessment
- 8.3 Information security risk treatment
Clause 9 – Performance Evaluation
This clause involves the processes required to monitor, measure, analyze, and evaluate the performance of the ISMS. It includes internal audits and management reviews. Key sub-clauses include:
- 9.1 Monitoring, measurement, analysis, and evaluation
- 9.2 Internal audit
- 9.3 Management review
Clause 10 – Improvement
This clause emphasizes the need for continual improvement of the ISMS. It includes corrective actions for nonconformities. Key sub-clauses include:
- 10.1 Nonconformity and corrective action
- 10.2 Continual improvement
Annex A – Reference Control Objectives and Controls
Annex A in ISO/IEC 27001:2022 lists a set of 93 controls, categorized into 4 themes. These controls are linked to ISO/IEC 27002:2022, which provides detailed guidance on the implementation of these controls.
The four categories are:
- A.5 Organizational controls (37 controls)
- A.6 People controls (8 controls)
- A.7 Physical controls (14 controls)
- A.8 Technological controls (34 controls)
Key Changes in ISO/IEC 27001:2022
- The control set in Annex A was reduced and reorganized into four themes, as opposed to the previous 14 domains.
- More focus on business and risk-based approaches.
- Updated terminology and definitions in line with ISO/IEC 27002:2022.
This structure provides a systematic and risk-based approach to managing information security in any organization.
ISO 27001:2022 requirements & controls
Defined within the ISO 27001 standard are ten requirements, including information security guidelines, requirements intended to protect an organisation’s data assets from loss or unauthorised access and recognised means of demonstrating their commitment to information security management through certification.
Requirement 6.1.3 (Information Security Risk Treatment) defines Annex A, specifying controls derived from ISO 27002:2022.
ISO 27001 also includes a risk assessment process, organisational structure, Information classification, Access control mechanisms, physical and technical safeguards, Information security policies, procedures, monitoring and reporting guidelines.
Annex (S)L Explained
“Annex L” defines a generic management system’s core requirements and characteristics. This is a critical point. Your company’s management system extends beyond information security.
While the focus of ISO 27001 is information security, the standard integrates with other ISO standards based on ISO’s Annex L, allowing you to introduce these standards to develop further and improve your overall management system later. They include ISO 9001 for quality management, ISO 22301 for business continuity management, ISO 227701 for Privacy protection and up to 50 other ISO standards.
Whilst we are not suggesting that you look at these standards for now, the point is that it is possible. You have an ‘upgrade path’ within ISO and ISMS.online (Integrated Management System) that won’t require reinventing the wheel when stepping it up to another level.
ISO 27001:2013 & ISO 27001:2022 –
What’s the difference?
In practical terms, very little has changed between the 2013 and 2022 ISO 27001 information security standards except for minor cosmetic points and additional requirements (9.3.1, 9.3.2, 9.3.3) and revised Annex A controls linked to ISO 27002:2022.
Transitioning to the New Standard
Organisations that have already achieved ISO 27001 certification must transition to the new version by October 31, 2025. This transition will require them to review and update their current ISMS to comply with the new requirements.
Overview of Changes Introduced in ISO 27001:2022
ISO 27001: 2022 brings with it several refinements and additional wording requirements. These changes ensure the standard remains applicable and updated with the latest security best practices.
The new version of the Standard requires organisations to ensure that their management systems comply with the updated requirements and to review any changes to the wording of the Standard to ensure they understand the implications for their security management systems. This includes changes to the language used, adjustments to the structure and content, and the addition of new clauses.
Restructuring of Annex A Controls in ISO 27001 2022
Following the release of ISO 27002:2022 on February 15, 2022, ISO 27001:2022 has aligned its Annex A controls.
The new version of the Standard draws upon a condensed set of 93 Annex A controls, including 11 new controls. A total of 24 controls were merged from two, three, or more security controls from the 2013 version, and 58 controls from the ISO 27002:2013 were revised to align with the current cyber security and information security environment.
Organisations must ensure that their information security management system meets the new requirements and that their existing controls are current.
To help with this, ISO 27002:2022 has made changes to the wording of some of the existing controls and added additional requirements for others. Additionally, the Standard now requires organisations to evaluate the performance of their information security management system and the effectiveness of the controls.
Control Categories and Attributes
Annex A controls have now been grouped into group categories:
- Organisational
- People
- Physical
- Technological
Each control has additionally assigned an attribution taxonomy. Each control now has a table with a set of suggested attributes, and Annex A of ISO 27002:2022 provides a set of recommended associations.
These allow you to quickly align your control selection with common industry language and international standards. The use of attributes supports work many companies already do within their risk assessment and Statement of Applicability (SOA).
For example, Cybersecurity concepts similar to NIST and CIS controls can be distinguished, and the operational capabilities relating to other standards can be recognised.
11 New Annex A Controls
The 11 new controls focus on cloud services, ICT readiness for business continuity, threat intelligence, physical security monitoring, data masking, information deletion, data leakage prevention, monitoring activities, web filtering and secure coding.

New Focus on Risk Treatment Processes
ISO 27001 2022 has placed a greater emphasis on risk treatment processes and the use of Annex A controls. The updated Standard now requires organisations to consider the four options for treating risks: modification, retention, avoidance and sharing. Two additional options for treating opportunities have been added: enhancement and exploitation. The Standard also outlines the need for organisations to consider risk sharing and acceptance in handling opportunities.
Organisations are now required to consider the consequences and likelihood of information security risks and the potential rewards of opportunities when assessing risk. The International Standard also encourages organisations to take risks if the potential rewards are more significant than the potential losses.
Overall, the new focus on risk treatment processes in ISO 27001 2022 provides organisations with a greater understanding of assessing and treating risks to minimise the potential for harm.
Evaluation of Third Parties
Organisations must ensure that third parties can provide adequate risk management measures, including but not limited to security, privacy, compliance and availability. Third parties must be aware of the organisation’s policies, procedures and standards and comply with them.
Organisations should perform periodic reviews and audits to ensure third-party compliance with security policies. They should also have a process for reporting and responding to security incidents resulting from the activities of third parties.
Organisations must ensure that all data and information assets under their control are securely returned or disposed of when terminating contracts or relationships with third parties.
Incident Logging Investigation and Recording
ISO 27001 2022 sets out specific requirements for logging, investigating and recording incidents. This includes organisations needing a process for logging security incidents and a procedure for investigating and documenting the investigation results. It is important for organisations to have a clear policy for logging and investigating incidents, as well as a process for recording the results of the investigation.
The policy should also cover the handling of evidence, the escalation of incidents and the communication of the incident to relevant stakeholders. The policy should also ensure that the organisation can quantify and monitor incidents’ types, volumes and costs and identify any severe or recurring incidents and their causes.
This will enable the organisation to update its risk assessment and implement additional controls to reduce the likelihood or consequences of future similar incidents.
Supplier Relationships Requirements
ISO 27001:2022 has introduced new requirements to ensure that organisations have a robust supplier and third-party management programme. This includes identifying and analysing all third parties that may impact customer data and services security and conducting a risk assessment for each supplier. The agreement between the supplier and service provider must also establish the relationship between them, and regular monitoring and reviews must be conducted to assess compliance.
Organisations must also ensure that supplier security controls are maintained and updated regularly and that customer service levels and experience are not adversely affected. In addition, personal data must be processed per data privacy regulations, and an audit of the supplier’s systems, processes, and controls must be conducted. By implementing these supplier management procedures, organisations can ensure they comply with ISO 27001:2022.
Clarification of Control Requirements for Externally Provided Processes and Products
Organisations must ensure that external services, products, and processes are appropriately managed and controlled. The 2022 version of ISO 27001 clarifies the requirements for externally provided processes and products.
Organisations must establish documented agreements with external providers and ensure that these agreements are regularly monitored and reviewed. Additionally, organisations must have a plan for responding to any inaccurate or incomplete information provided by external services or products and a procedure for handling any identified vulnerabilities in externally offered services or products.
Organisations must also ensure that the associated risks are appropriately managed and that the control of externally provided processes and products includes appropriate measures for security assurance and management of changes to documents, agreements, and procedures.
Supplier Management Procedures
ISO 27001 2022 introduces several changes to how organisations manage their supplier relationships. The revised Standard requires organisations to develop a formal supplier management policy and procedures, segment their supply chain into categories based on the value and risk of the relationship, and develop close working relationships with high-value suppliers:
Organisations must also take a risk-based approach to supplier selection and management, wrap information security policy for suppliers into a broader relationship framework. ISO 27001 2022 emphasises managing ICT suppliers who may need something additional instead of the standard approach.
Organisations must ensure supplier staff are educated, aware of security, and trained on organisation policies. Records of supplier management, including contracts, contact, incidents, relationship activity and risk management, must also be kept. All of this must be done to ensure an agreed level of information security and service delivery is maintained in line with supplier agreements.
Employee Cybersecurity Awareness
Organisations must take action to ensure that employees are aware of their responsibilities when it comes to cyber security.
Companies should focus on preventing human error by empowering staff to understand the importance of cyber security. Businesses should also invest in appropriate cybersecurity training programs and develop clear policies and procedures that detail what is expected from employees.
Furthermore, companies should incorporate cyber security into everyday operations and establish a culture of cyber security where staff feel comfortable and empowered to raise cyber security issues. By taking these steps, organisations can ensure that their employees know their responsibilities and are better prepared to protect their data and networks from cyber threats.
Establishing Controls for Human Resource Security in ISO 27001:2022
ISO 27001 2022 has introduced several new and refined controls for Human Resource Security. This includes the need to establish clear guidelines for personnel screening, terms and conditions of employment, information security awareness, education and training, and disciplinary processes. It also requires organisations to have a policy on using cryptographic controls and a formal starter, leaver, and mover process.
These controls are essential for protecting the organisation’s interests, as they help to ensure that all personnel have the necessary security clearance and are aware of their responsibilities. Furthermore, they help to ensure that confidential information is protected from unauthorised access and that any information security events are reported and dealt with appropriately. Implementing these information security controls is essential for any organisation seeking certification from an accredited certification body.
Understanding the Requirements of Interested Parties
ISO 27001:2022 has a specific focus on understanding the needs and expectations of interested parties. Interested parties are stakeholders, such as employees, shareholders, government agencies, clients, media, suppliers and partners interested in the organisation’s information security and business continuity. Identifying these stakeholders and their requirements is essential to develop an effective ISMS or BCMS.
A procedure should be written to clearly define who is responsible for identifying all interested parties and their legal, regulatory, contractual and other requirements and interests, as well as who is responsible for updating this information and how often it should be done. Once the requirements are identified, assigning responsibility for meeting them is essential.
Where do I start with ISO 27001 Certification?
Achieving ISO 27001 Certification can be complex and overwhelming but our ISMS.online software changes all that. Now you have pre-configured information security frameworks, tools, and content to help you achieve ISO 27001 success quickly and simply.
Imagine too, if you had a helping hand that guided you through each step of ISO 27001, without the need for expensive consultancy fees? Our ISO 27001 Virtual Coach package does just that.
You will find helpful videos from those that are ‘living’ ISO 27001, together with an information security specialist, as well as lots of hints and tips for success.
All delivered right where you need it most, inside the ISMS.online platform allowing you to work where and when you want, at your own pace towards achieving your goals.
How do I achieve ISO 27001?
The core requirements of the information security standard are addressed in clauses 4.1 through 10.2, and Annex A controls you may choose to implement, subject to your risk assessment, risk treatment plan and work, are covered in A.5.1, and 5.31 through 5.36 and A. 8.8 (found at the bottom of this page).
If you want to achieve ISO 27001, you will be expected to meet all the core ISO 27001 requirements. One of the fundamental core requirements (6.1) is to identify, assess, evaluate and treat information security risks. Out of that risk assessment and management process, the ISMS will help determine which of the ISO 27001 Annex A reference control objectives (information security controls) may need to be applied to manage those information security-oriented risks.
Some organisations may not take their Information Security Management System to certification but align to the ISO 27001 standard. This might be okay to meet internal pressures however delivers less value to key stakeholders externally, who increasingly look for the assurances a UKAS (or similar accredited certification body) independently certified ISO 27001 delivers.
ISO 27001 certification
For organisations looking to demonstrate their commitment to information security, certification from an accredited body is the way to go. The process of seeking certification requires a thorough review of the organisation’s ISMS and its ability to comply with the requirements of ISO 27001:2022.
An accredited third-party auditor should conduct the certification process, who will review the organisation’s ISMS and assess its compliance with the Standard. The auditor will also provide recommendations for improvements and ensure the organisation can meet the new requirements of the Standard.
Once the certification process is complete, the organisation will receive an official certificate from the accredited body.
